SWI Pick #12 - Fortinet (FTNT) The Most Sleep Well Investment In Cyber Security [Part 1]
Leveraging a leadership position in networking security to grow into adjacent markets, promises a 15%+ forward growth for the next 5 years, and trading at 4% FCF yield.
I am Trung. I deep-dive into exceptional businesses. I follow up on their performance with my Thesis Tracker updates, and when the right price comes, I buy them for the Sleep Well Portfolio, which I am building for my daughters to redeem in 2037. I disclose my reasoning for all BUY and SELL (ideally never) transactions (1st, 2nd, 3rd, & more). Access all content here.
Hi, sleep well, investors,
Enjoy a comprehensive deep dive on Fortinet (FTNT), the ‘safest’ bet in cyber security.
Executive Summary [Part 1]
Simplifying the Business and Cybersecurity Industry
Why is it a Sleep Well business? [Part 2]
Purpose-built hardware and OS combo on a unified console
Predictable, diversified, and enduring business model
Favorable position to grow to adjacent areas
Stable competitive advantages
Founder led management
Anti-fragile attributes
What can go wrong?
Fair price to own
Sleep Well Score
What to track
Executive summary
Key sleep-well ingredients
FTNT’s core offerings combine essential networking hardware (switches, routers, firewalls) and sticky software-as-a-service ‘SaaS’ (network security) to help enterprises build, manage, and secure their IT infrastructure. The superior performance and cost benefits vs peers drove the company to the leader position in network security from a challenger position a decade ago (Gartner 2011 vs. 2023).
In my opinion, Fortinet’s core offerings face the least disruptions and are more future-proof than other cybersecurity areas. First, no matter how enterprises organize their IT infrastructure, they always need networking hardware, especially the best-of-class ones. In 2022, IDC reported that 50% of global shipments of networking firewall appliances were Fortinet’s. Next, organizations will always prefer to keep key assets, applications, and workloads on-premise. This is especially true for regulated, data-sensitive, and latency-sensitive industries, supporting a respectable 10-year growth rate between 5% and 15%. Moreover, when employees work in the office, accessing data and applications in a local network system is safer and faster.
Fortinet’s core offering is also future-proof because there is no ‘one’ way to protect an enterprise’s infrastructure. All solutions have security gaps, and adversaries evolve in real time. What’s more, Gartner reports little desire for an organization to be protected by just one vendor. Thus, it’s unlikely Fortinet’s offerings will be obsolete.
FTNT also has room to grow. Its expansion to SASE Cloud Security and Security Operations has been successful for five years and is positioned to maintain 15-20% growth for the next 5-10 years. It’s a hyper-competitive market, but Fortinet has a good pathway to maintain/gain market share.
Management is founder-led and measured in capital allocation - focusing on organic growth in high-probability avenues, preferring to acquire lands and buildings to house its data centers (vs. renting), and returning capital to shareholders with an 11.4% buyback yield ($5.3B) since FY2020, 3%+ a year.
FTNT boasts the best business model with the highest margin profile in the industry, at 77% gross and 28% operating margin. It has been free cash flow positive since its IPO in 2009. As we advance, its moats and market share are well protected by integrated hardware and software offerings, which are centrally managed and have a consistent leadership ranking on Gartner for network security.
The current market expectation implies a 9% growth over the next decade, which I believe is low given the broad industry growth rate is already 15% in the next five years. FTNT stock will not rocket one’s portfolio but will help one sleep well.
Key risks
Palo Alto is a formidable competitor in the broader cybersecurity landscape. Its aggressive ‘platformization’ strategy may cause pricing pressure.
Meanwhile, Microsoft and CrowdStrike's rapid growth, albeit from a different angle, will pressure Fortinet to take more risks.
Nevertheless, the market is vast and unfragmented, with over 3500 companies; network appliances and firewalls are permanent real estate in enterprise networks, and there is no one sure way to secure the entire IT system. It’s not winner-takes-all. Conservative investors can own multiple winners to diversify the risk. I own CrowdStrike (my largest position) and plan to own FTNT and (maybe) PANW when the price is right.
What is Fortinet
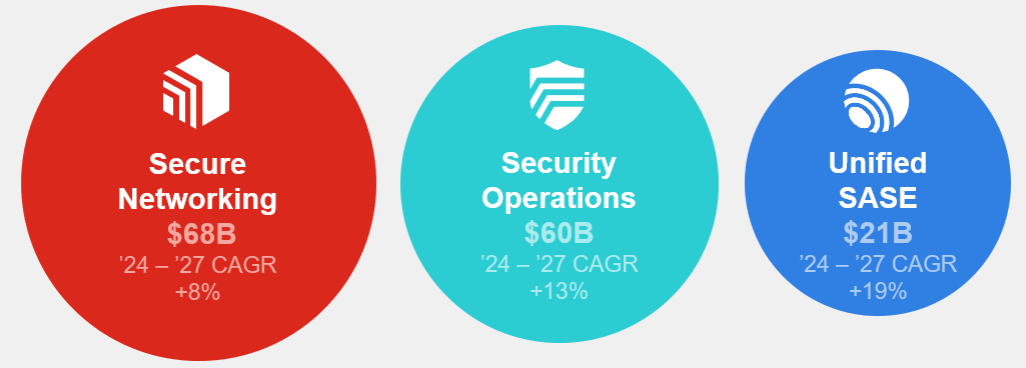
Fortinet (FTNT), with a $48B enterprise value, is a leader in the $68B secure networking market and is venturing successfully into the $81B cloud security market. The combined opportunity is estimated to grow over $200B TAM per annum (TAM) by 2027 (Gartner, 2023).
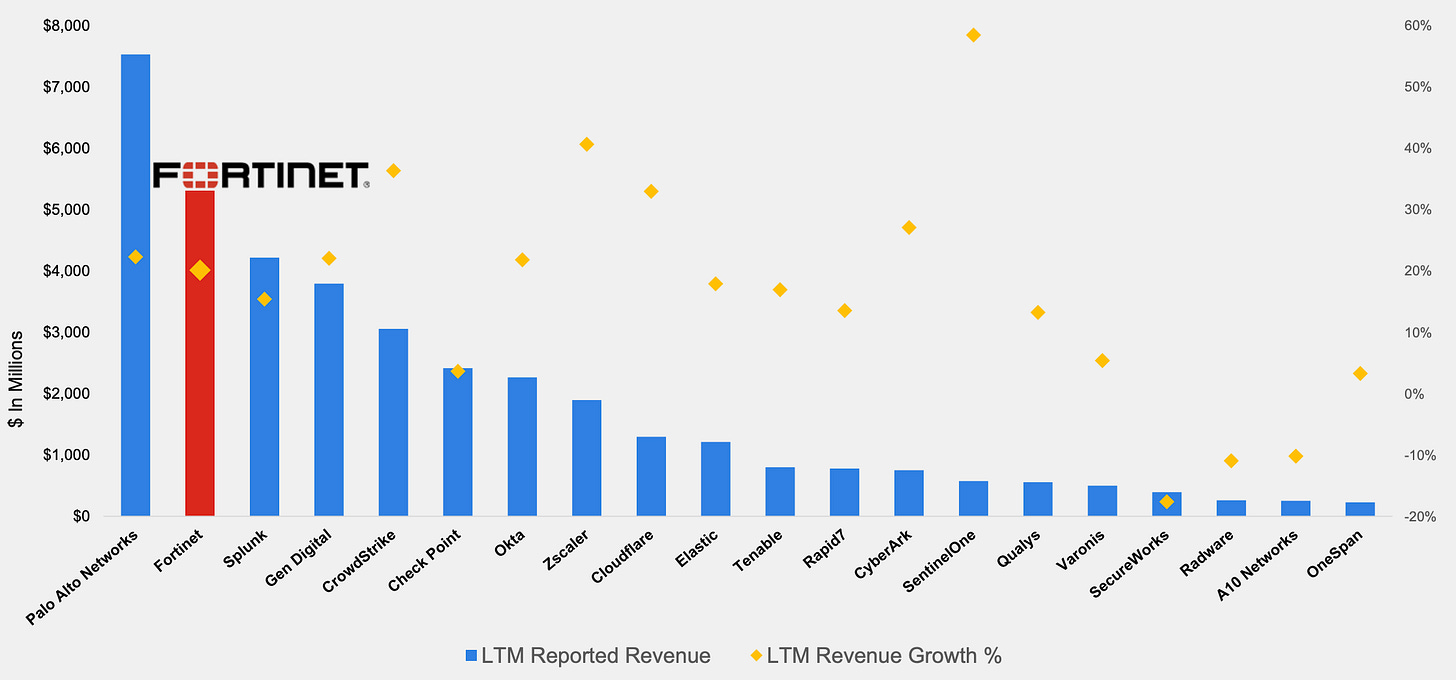
The market is huge; it has just a 4% market share despite being the second-largest pure-security player behind Palo Alto, which has a 6% market share.
All the players above focus on slightly different security areas with some overlaps; you will see the what and why later. Returning to Fortinet, its business offers a platform called Fortinet Security Fabric, which covers three security areas: Secure Networking, Unified SASE, and Security Ops with a 70/21/10 split, respectively. Below, you can see the offerings under each security category.
Source: Investor presentation Mar 2024
Fortinet Security Fabric takes a holistic approach to security. Through a single console, the network landscape is visible and protected, and all devices are integrated into a centrally managed and automated defense.
In terms of reporting segments, Fortinet categorizes its revenue into Product and Service segments. Product predominately covers secure networking areas, and services cover the SASE and SecOps areas.
Product revenue is the sales of essential networking appliances, such as switches, routers, and firewalls that block malicious traffic before entering private (on-premise) networks.
Before learning about Fortinet, I never knew there were so many types of firewalls. I also never knew there were firewalls for containers (a virtualized operating system run for selective applications) or points of presence (clouds on the edge). However, as the enterprise's perimeter expands, the type of firewalls also expands. By 2025, 60% of organizations will have more than one type of firewall.
What’s special about Fortinet appliances is that they have purpose-built security ASIC processors and operation systems (FortiOS) to ensure superior stability, performance, and interoperability. Fortinet, IDC, and Gartner's industry report verify some of these claims. For context, Forrester’s Total Economic Impact study reveals 318% ROI and $10.6M in cost benefits achieved with the Fortinet Data Center solutions.
On top of the physical firewalls, Product revenue also includes the sales of Enhanced Platform Technology products, such as email security, cloud security, and endpoint protection.
Service revenue is the higher-growth SaaS subscription revenue (1-5 year contract), mainly serving the newer security services in SASE (secure access service edge) and SecOps (security operations).
SASE enables secure access to applications on any cloud (private, public, hybrid, mixed) with solutions including Firewalls, SD-WAN, Secure Web Gateways, Cloud Access Services Brokers, Data Loss Prevention, Zero-Trust Network Access, and cloud security, including Web Application Firewalls, Virtualized Firewalls, and Cloud-Native Firewalls, among other products. There are many acronyms, but don’t worry; these will make more sense in the industry overview section.
These functions are delivered through the FortiOS operating system and managed through a unified management console.
As Fortinet has visibility of the data and applications on the cloud that flow through Fortinet’s network appliances, it also offers AI-powered (automated) application / data / endpoints detection and response services. Where AI can’t do the job (yet), Fortinet offers expert services such as managed detection and response (MDR), Security Ops (SOC), and security information event management (SIEM).
Fortinet Security Fabric is a broad and holistic platform approach similar to CrowdStrike’s Falcon or Palo Alto’s Prisma and Cortex. It collects security information centrally to design applications that detect, prevent, and respond to threats. All start with a core focus (CrowdStrike—endpoints), then leverage the data to expand to other security areas.
How do they differ, and why have I chosen Fortinet as a preferred business to invest in at the current price?
Let’s examine the $200B security landscape and how Fortinet positions vs. other key players: Palo Alto (PANW), Microsoft (MSFT), Zscaler (ZS), CrowdStrike (CRWD), Datadog (DDOG), Okta (OKTA), Snowflake (SNOW), Oracle (ORCL), Cisco (CSCO) and Sentinel One (S).
The cybersecurity landscape
First, why do we need cybersecurity?
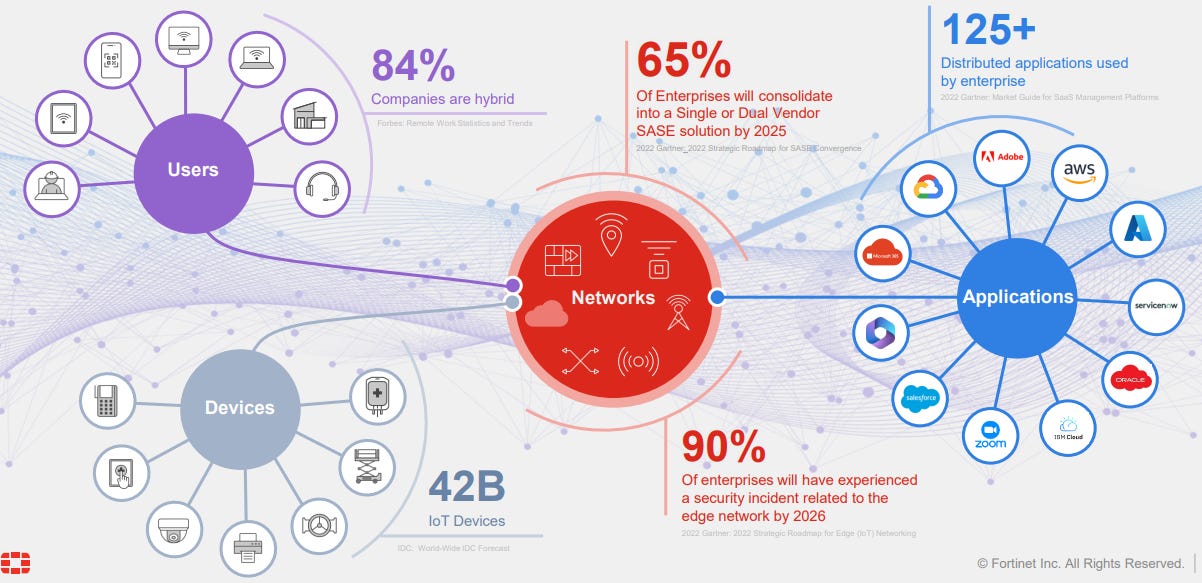
The diagram below shows how the enterprise IT system connects users, devices, networks, and applications. The move to the cloud, widespread mobile adoption, remote work (84% of companies are hybrid), and increasing enterprise software applications have enabled technology innovations and productivity. However, they have also created more access points for bad actors to infiltrate the enterprise.
Strikingly, 90 million people are affected by cybercrime yearly, costing the global economy over 2 trillion dollars (Cybercrime magazine). As we enter the Generative AI stage, new kinds of attacks or even a new model called Ransomware-as-a-Service (RaaS) will sprout, making it even easier and cheaper (only $50/month) for attackers to cause harm to a victim. Meanwhile, it takes 21 days to detect a breach and costs an average of $9.4M each time to remediate.
Despite the substantial damage and disruption, security spending is only at $200B each year, a 10th of the total damage. The budget needs to rise.
Expanding threat surface and ways to protect the enterprise network
Cybersecurity is essentially the protection of data. It is the most valuable asset, whether personal information, trade secrets, or digital money.
However, data flows through everything: the networks (on-premise or on the cloud), applications (from development to deployment and upgrading), devices (endpoints, IoT, OT), and hardware (infrastructure, data center servers) and is used by various actors (people/identities).
As everything is interconnected, a vulnerability in one area is a security risk for the whole system. Hence, protecting the enterprise requires a holistic approach and protection of all areas. CrowdStrike breaks it into six.

Networks
I’ll start with networks. Networks are considered the most critical part of enterprise security. They are akin to the body's nervous system; they facilitate signals/data flow between hardware, software, and people in different locations.
Network security protects users whenever they click on a URL, connect to a hotspot / wifi / wireless, visit a website link, run an application, or access their company’s network. Hence, network security monitors traffic requests from the company’s network to stop threats before they materialize.
Historically, firewalls were sufficient to protect an enterprise, as its data and applications were limited to one location. However, enterprises now have multiple locations and require communication with external networks and on the cloud with little visibility. Attackers have also found new ways to break through this moat around the physical/virtual locations. There have to be better ways.
SASE—Secure Access Service Edge (blue box below)—was born to protect traffic on the edge - a term that describes the people (the left of the diagram below) and the resources they access—applications/data/devices (right) on the cloud.
However, SASE is not sufficient. The protection only works when requests are routed through the firewall, SWG, or VPN. The latency caused by these central choke points was untenable. Additionally, firewalls can not tell if a person identified is who they said they were or if the application is fully secured before entering the network.
As a result, new ways of securing the enterprise network came about to observe and analyze at source, i.e., the people, and continuously learn the deep context of how they use resources such as data, applications, and devices to differentiate between a threat and a secure connection.
Let’s look at them one by one.
Identity/people:
People are the weakest link. Hence, it’s imperative that the people accessing the enterprise network are the right users and that they only access the right resources at the right time for the right reasons.
This approach to tackling security at the source is called a zero-trust network architecture. All users, whether in or outside the organization's network, must be authenticated and authorized before being given appropriate access to the network. It emphasizes trusting no one and continuously validating the person at every stage of their digital interaction.
Identity and Access Management (IAM) is one solution for building a zero-trust architecture. It revolves around verifying human identity and behavior—asking who you are, what company resources you can access, and your typical behavior (vs. fraudulent bad actors with false identities).
Fortinet has developed FortiNAC and FortiAuthenticator applications for its networking appliances to identify devices and users on the network and see how they use these applications. However, Okta (OKTA) is the dominant vendor with the most advanced solution. I wrote about the company and technology in 2021 if you want to know more.
The other solution to tackle the weak link in people is to layer in an additional function called Security Operations (SecOps). SecOps can be applied to other security areas, too (devices / applications / data), because these are security analysts and technologies directly involved with capturing and analyzing security information, correlating security log data to identify security incidents, and responding to cyberattacks within an enterprise. Fortinet offers Security Ops with SOC-as-a-service and SIEM, but Splunk, acquired by Cisco, is the leader in this space.
Devices (endpoints)
The other weak link is devices. That’s mobile, laptops, IoTs, factory sensors, or any devices that send signals to the network. Working from home and higher cloud adoption means more personal devices (unsecured) have access to enterprise networks, creating more gateways for bad actors to exploit.
An anti-virus application is installed on the device to prevent an attack on the endpoints. The application monitors, records, and stores activities, and when malware or threats are detected, a patch is created to deal with the attack. This basic layer of protection is called Endpoint Detection and Response (EDR).
The next evolution is called XDR (Extended Detection and Response), which aims to go beyond the endpoint by integrating, correlating, and contextualizing data from multiple enterprise areas (like email, application, identity, network, etc.) beyond the endpoint to provide advanced detection and response against more sophisticated threats.
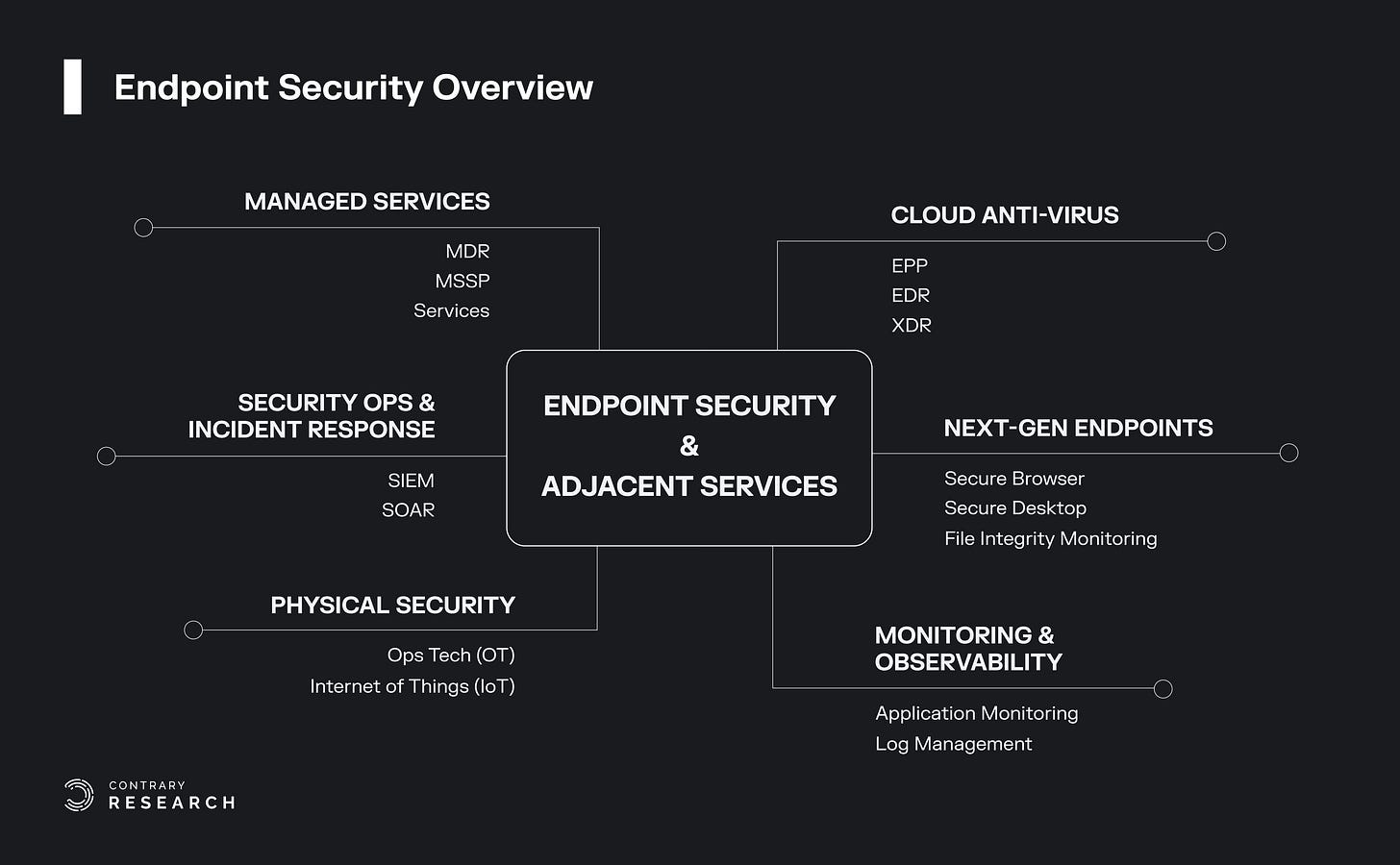
This has given birth to adjacent endpoint subsectors such as managed detection and response (MDR), security information event management (SIEM), security orchestration, automation, and response (SOAR), and external attack surface management (EASM). Meanwhile, Operational Technology and Industrial IoT endpoint devices are also gaining traction, increasing the importance of SecOps.
The total market size of these segments is estimated to reach $125B in 2025 (CrowdStrike).
Source: Contrary Research, 2022
Who are the key players?
CrowdStrike is the current leader (top spot on Gartner 2023). It provides a light agent (30MB vs. 1GB+) that is fast and easily installed on devices and runs real-time data threat analysis on the cloud (diverting the heavy workload away from the device), displacing the legacy technology from Trend Micro, McAfee, and Symantec, whose solutions are on-prem, and with the heavy agent on the device, they are slower and less effective. Other key vendors include SentinelOne, Cybereason, and Palo Alto Networks Cortex EDR.
Applications
Applications or software can also be vulnerable to attack, especially when over 90% of codebases and applications utilize open-source software. Bad actors can inject malware into codes, steal data, or make unauthorized changes to penetrate the enterprise network. The recent SolarWinds malware attack is a prime example of how costly it can be when codes are not secured. It infected over 18,000 systems worldwide, causing irreparable damage worth billions of dollars.
Hence, to secure applications, one can apply / test security features throughout the development process (shift-left) and/or after it has been deployed (shift-right) to prevent security vulnerabilities.
Shift-left aims to tackle problems at the root (source code), preventing risks in the earliest stages of software development. Thus, security features such as secure coding, vulnerability scan, and static application security testing (SAST) are implemented during the application's source, design, build, testing, and packaging development. See the flow chart below.
Shifting-right protects applications by testing and monitoring them continuously once deployed in real life (full use) to detect and block common application attacks, like SQL injection and command injection. It features technologies to monitor applications to see how they communicate with others (API/WAF), analyze patterns and behavior, and how the threat landscape changes.
Securing application development on the cloud is becoming more mission-critical. The IDC estimates that 750 million new cloud-native apps will be created globally by 2025, representing 4x growth. However, the challenge is that only one in five companies reports having the tools, security measures, and automation to scale. This has led to the rise of DevOps to help automate the software delivery workflow from code to deployment. GitHub and GitLab are leaders.
GitLab allows software developers to automate the steps required to check code, generate code, and automate security testing. You can see the details below:
Data
Essentially, all of the solutions above protect data in one way or another. These security tools protect data through data masking, encryption, and redaction of sensitive information. They also go further by collecting vast amounts of data from websites, applications, sensors, devices, etc., which gives IT teams the ability to aggregate and visualize data and find patterns to understand how breaches happen, how companies stay compliant, and alert potential bad behaviors before they happen.
Data security can be simplified into three categories:
data
governance
vulnerability management and assessment
Data: Solutions aim to prevent the leakage, transmission, or loss of sensitive data from an enterprise. As 40% of ransomware attacks are through email, minimal technologies are required, such as spam filtering, quarantine capabilities, URL rewriting, and antivirus software. Other solutions scan structured and unstructured data to identify, search, index, track, and analyze sensitive data so that if a data breach occurs, they can work out how it was breached/how it happened.
Governance, risk, and compliance (GRC) aims to synchronize risk management into a centralized function to help prevent or respond immediately to a breach or cyber-attack.
Vulnerability management and assessment aims to identify, classify, prioritize, and mitigate data vulnerabilities. This concept also applies to applications, devices, and infrastructure. For example, VM technologies (private) utilize software agents installed across an enterprise’s network appliances, servers, endpoints, and applications to constantly scan and discover security gaps, misconfiguration, and potential vulnerabilities. It can also stress-test corporate environments against popular cyberattacks.
Rapid7, Tenable, and Qualys are the three players specializing in this space. However, with their vast data visibility, Snowflake (SNOW), Datadog (DDOG), and Databricks are also vying for a path into data security.
Summary
As the enterprise ecosystem grows, so does the security. Hence, there are over 3,500 vendors currently available.
Francis (Software Analyst) drew up the chart of the key players in each category. Some you will recognize from the overview. How do you decide what business to own?
There are two ways to get exposure to this 15% CAGR growth industry.
Own the largest platform (Microsoft, Palo Alto) with the broadest solutions.
Own best-in-class solutions (* - my preferred choice)
Network (Fortinet*, Checkpoint, Palo Alto*, Zscaler)
Endpoints (CrowdStrike*, Sentinel One)
Data (Datadog*, Snowflake*, Databricks, Rapid7, Qualys)
Identity (Okta*, CyberArk)
It’s also important to bet on companies exposed to the most durable trends.
According to the recent CISO report (chief information security officer), network security is the top priority in the coming 12 months. Identity (the weakest link of the enterprise) is second, and cloud infrastructure security (data centers) is third. These are also the areas with the largest skills gap.
The result is consistent with a similar study conducted by Battery Ventures, which showed network security, email, cloud, and data as the top priorities.
Meanwhile, most of the security budget goes to data, application, cloud, and endpoint security. CISOs look to prevent threats in the earliest stages of software and data development and at entries (endpoints).
What’s your pick?
My choice is Fortinet, with Palo Alto as a good alternative.
The reasons I pick Fortinet over others are:
Networking appliances are must-haves. Meanwhile, Fortinet is the leader, shipping 50% of global firewall appliances, and will remain the customers’ choice.
Network security is also a must-have. It’s arguably the most effective area for protecting the enterprise, and Fortinet is also the customers’ choice, next to Palo Alto.
Fortinet’s ongoing expansion to SASE and SecOps has yielded good results, and it is planting the seeds in application, data, and endpoint security.
Fortinet’s historical growth has been organic, so additional levers in inorganic growth can propel the business further.
Fortinet is also founders-led and has been conservative but consistent in delivering strong above-market performance.
Let’s go into detail in Part 2 of the write-up.
*Additional disclosure: I already own CrowdStrike, the best-in-class Endpoint protection provider in the cloud's largest (and most competitive) market. You can follow my Crowdstrike FY2024 update, read my Q2'24 review, first note in 2020, and deep-dive in 2021 (pre-sleep well framework).
Part 2 explains why Fortinet is a Sleep Well business.
Executive Summary [Part 1]
Simplifying the Business and Cybersecurity Industry
Why is it a Sleep Well business? [Part 2]
Purpose-built hardware and OS combo on a unified console
Predictable, diversified, and enduring business model
Favorable position to grow to adjacent areas
Stable competitive advantages
Founder led management
Anti-fragile attributes
What can go wrong?
Fair price to own
Sleep Well Score
What to track
Your support 🥰 in spreading the word allows me to do what I do best—sifting through the haystack for market leaders, saving you time from turning over your portfolio.
Check out my most recent BUY and all other sleep-well investments writeups here.
Tickers mentioned: CRWD 0.00%↑ MSFT 0.00%↑ S 0.00%↑ OKTA 0.00%↑ PANW 0.00%↑ FTNT 0.00%↑ ZS 0.00%↑ NET 0.00%↑ CSCO 0.00%↑ ORCL 0.00%↑

















I bought the stock today - check out this post for details: https://www.sleepwellinvestments.com/p/5th-live-trade-alert?r=8u09c&utm_campaign=post&utm_medium=web
Part 2 is out - https://www.sleepwellinvestments.com/p/a-sleep-well-investment-in-network